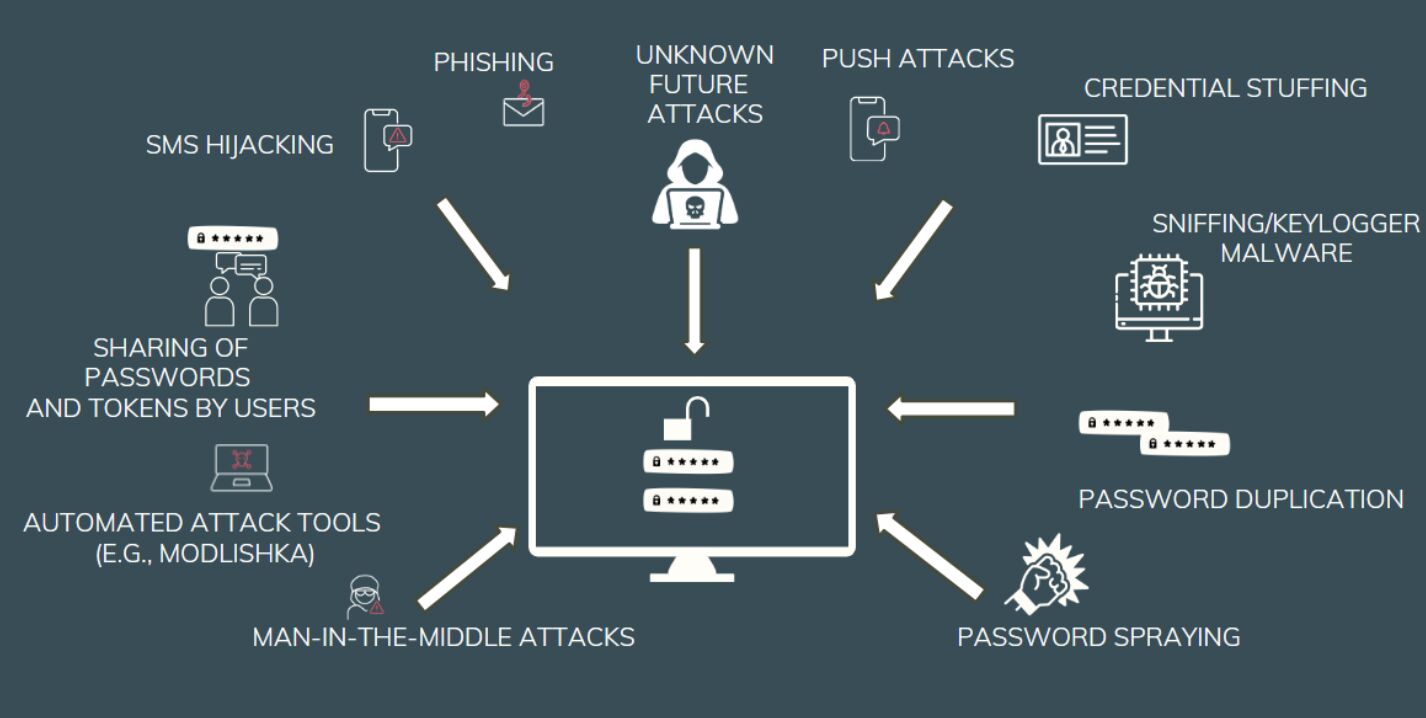
Cyber attackers use multiple methods (over 30 listed) to bypass identity protection, passwords, and traditional multi-factor authentication, while Veintree's highly secure authentication (and not identification) system protects you by making these attacks unfeasible due to the very nature of the authentication required.